Registry hacks refer to modifications made to the Windows Registry, a hierarchical database that stores low-level settings for the Microsoft Windows operating system and for applications that opt to use the registry. These modifications can alter system behavior, appearance, and performance.
Purpose of Registry Hacks
Users implement registry hacks for various reasons:
- System Customization: Tailoring the user interface, context menus, and other visual or functional aspects beyond standard settings.
- Performance Optimization: Tweaking parameters to potentially improve system speed or resource management, though results can vary and require careful consideration.
- Enabling Hidden Features: Unlocking functionalities not exposed through the standard graphical user interface.
- Troubleshooting: Directly addressing specific system issues or errors by modifying relevant registry keys, often as guided by technical support.
- Feature Management: Disabling or enabling specific Windows components or services.
Critical Precautions for Registry Modification
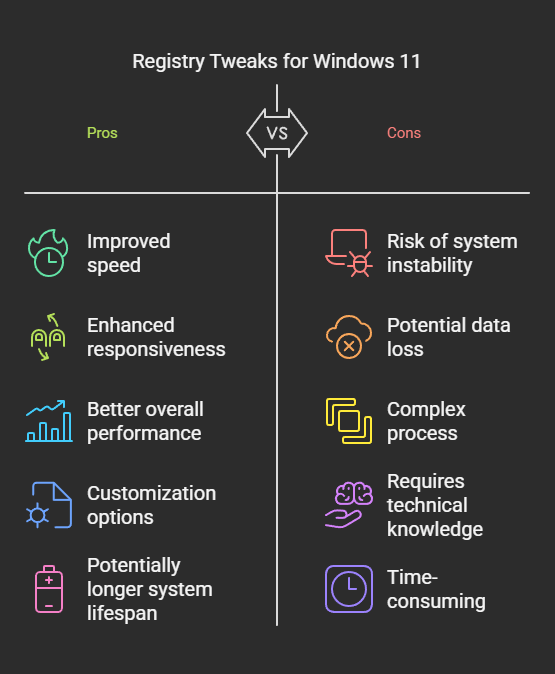
Modifying the Windows Registry carries significant risks. Incorrect changes can lead to severe system instability, application malfunctions, or even render the operating system unbootable. Always observe the following precautions:
- Backup the Registry: Before making any changes, create a full backup of the registry. The Registry Editor (*) allows exporting the entire registry or specific branches.
- Create a System Restore Point: A system restore point can help revert the system to a previous state if issues arise.
- Understand the Modification: Never apply a registry hack without fully understanding what it does and its potential consequences. Research thoroughly.
- Use Reliable Sources: Obtain registry hacks only from reputable and trusted sources. Unverified modifications can be malicious or damaging.
- Modify Specific Keys Only: Change only the keys and values specified. Avoid altering unrelated entries.
- Document Changes: Keep a record of any modifications made, including the original values, to facilitate reversal if necessary.
Common Areas for Registry Hacks
Registry hacks can target a wide array of system functionalities. Common areas include:
- Context Menu Management: Adding custom commands or removing unwanted entries from the right-click context menu for files, folders, or the desktop.
- User Interface (UI) Tweaks: Modifying elements such as icon spacing, taskbar behavior, window animations, or font rendering.
- File Association Control: Manually defining or altering which applications open specific file types.
- System Behavior Adjustments: Changing how Windows handles startup processes, error reporting, or network settings.
- Security Enhancements: Implementing stricter security policies, such as disabling certain protocols or features, although this often requires deep expertise.
- Privacy Settings: Modifying telemetry and data collection settings beyond what is offered in the standard UI.
Methods of Applying Registry Hacks
Registry modifications are typically applied in two primary ways:
- Manual Editing via Registry Editor (*): This involves navigating the registry structure, finding specific keys, and then creating, modifying, or deleting values directly. This method requires precision and a clear understanding of the registry path and data types.
- Using .REG Files: Registry export files (.REG) contain predefined registry changes. Double-clicking a .REG file and confirming the import prompt will merge its contents into the registry. This is a common way to distribute and apply pre-configured hacks, but the source of the .REG file must be trustworthy.