Understanding Vega Scanner
Vega is a free and open-source web vulnerability scanner and testing platform. It is designed to help security professionals and web developers identify and validate security vulnerabilities in web applications. Built using Java, Vega offers a graphical user interface (GUI) and runs on Linux, OS X, and Windows.
Core Functionalities
Vega provides two primary modes of operation:
- Automated Scanner: This mode allows for quick and automated tests against a specified target. It crawls the website, analyzes content, and launches various detection modules.
- Intercepting Proxy: Vega can function as an intercepting proxy, allowing users to monitor and manipulate HTTP/HTTPS traffic between their browser and the web server. This is useful for manual inspection and fuzzing.
Vulnerability Detection Modules
Vega comes equipped with a set of detection modules designed to identify common web application vulnerabilities. These modules are written in JavaScript and can be customized or extended by users. Key vulnerabilities Vega tests for include:
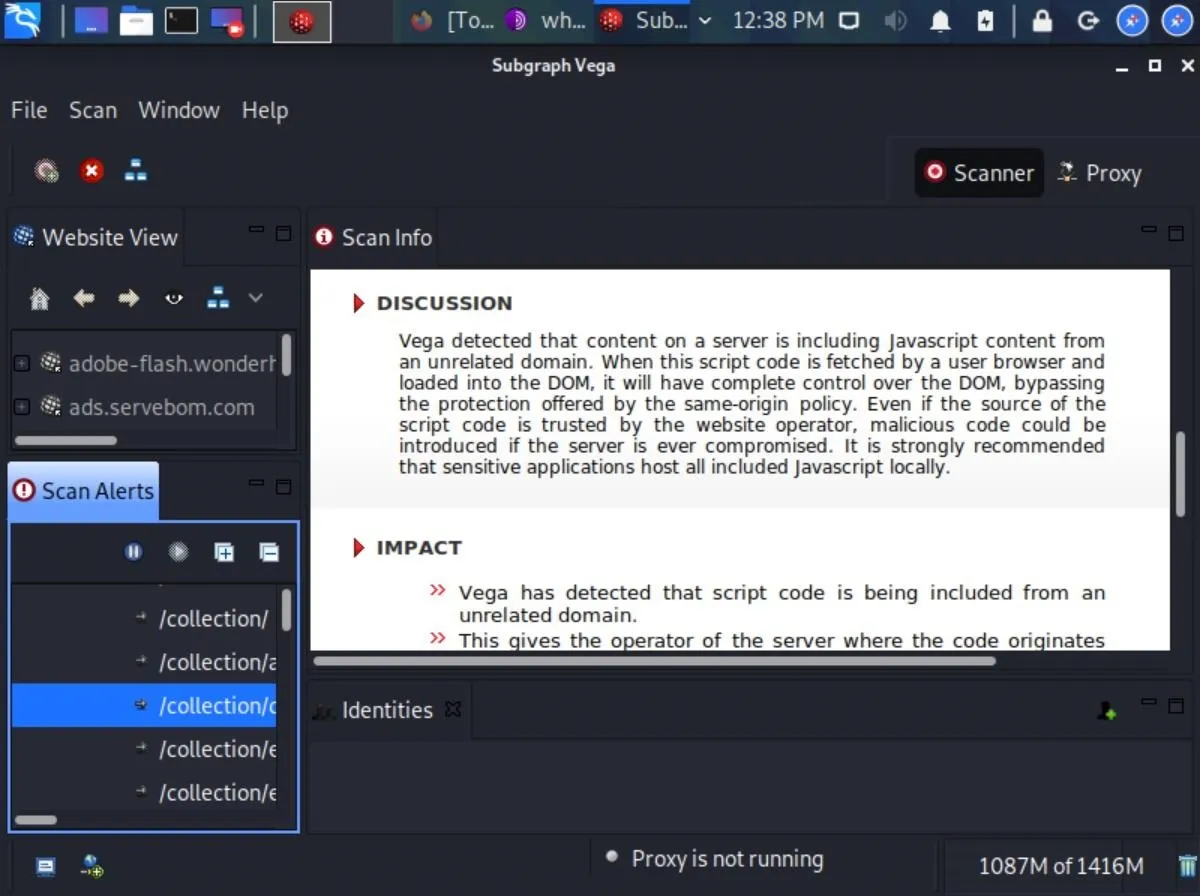
- Cross-Site Scripting (XSS): Both reflected and stored.
- SQL Injection (SQLi): Including blind SQL injection.
- XML Injection (XXI) / XXE (XML External Entities).
- Shell Injection.
- Remote and Local File Inclusion (RFI/LFI).
- Directory Traversal.
- Sensitive Data Exposure / Information Leakage.
- Weak Authentication Mechanisms.
- Insecure Session Management.
Key Features
- Intuitive GUI: Provides a user-friendly interface for configuring scans, viewing results, and managing alerts.
- Customizable Scans: Users can fine-tune scan parameters, select specific modules, and define authentication credentials.
- Alert System: Detected vulnerabilities are presented as alerts with varying severity levels (High, Medium, Low, Info). Each alert provides details about the vulnerability, the affected parameter, and evidence.
- Request/Response Viewer: Allows detailed inspection of the HTTP requests sent by Vega and the responses received from the server.
- Extensibility: Advanced users can create new attack modules using JavaScript to test for custom or newly discovered vulnerabilities.
- Session Management: Supports various authentication methods, including form-based authentication and cookies, to test applications that require login.
Benefits of Using Vega
- Cost-Effective: Being open-source, Vega is a free tool, making it accessible for individuals and organizations with limited budgets.
- Cross-Platform: Runs on major operating systems due to its Java-based architecture.
- Educational Tool: Its proxy mode and detailed alerts make it a good tool for learning about web application security vulnerabilities and how they are exploited.
Important Consideration: Always ensure you have explicit, written permission before conducting any vulnerability scanning or testing on web applications or systems that you do not own. Unauthorized scanning can be illegal and unethical.